SAML 2.0 Authentication connection
We have added supports for a bunch of new values from metadata:
- Other signing certificates: it contains all the signing certificates from the metadata. These are used by Safewhere*Identify to verify signatures of messages which the Identity Provider sends to Identify
- Find value: The value of the attribute that is used by Safewhere*Identify to search for the certificate, e.g. its subject or thumbprint.
- Get certificates button: Allow users to select a new certificate.
- Find type: Specifies which certificate attribute that is used to match against the find value. A common way to locate a certificate is to search for its subject distinguished name or its thumbprint. The authentication connection will use the first certificate that matches the specified search criteria. Possible values are: FindByThumbprint, FindBySubjectName, FindBySubjectDistinguishedName, FindByIssuerName, FindByIssuerDistinguishedName, FindBySerialNumber, FindByTimeValid, FindByTimeNotYetValid, FindByTimeExpired, FindByTemplateName, FindByApplicationPolicy, FindByCertificatePolicy, FindByExtension, FindByKeyUsage, FindBySubjectKeyIdentifier.
- Store location: The location of the certificate store to use. Possible values are: CurrentUser, LocalMachine
- Store location name: Specifies which certificate store the certificate is placed in. Possible values are: My, TrustedPeople.
- In store?: This is a computed field which indicates if the certificate can be found based on what the user specified for the other signing certificate elements. The value is updated upon refresh of the page, so if you want to check if your values where correct, you should save the connection and see if the checkmark is ticked.
- Keyname: This specifies the keyname of the certificate.
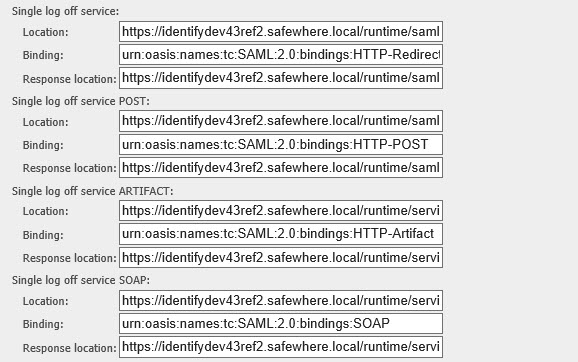
- Single log off service:
- Binding: The binding that Safewhere*Identify should use to receive log off requests: “urn:oasis:names:tc:SAML:2.0:bindings:SOAP”, “urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect”, “urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST”, “urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact”.
- Location: The endpoint to which Safewhere*Identify should send log off requests via the above input binding.
- Response location: The endpoint to which Safewhere*Identify should send responses for log off requests via the above input binding.
- Artifact resolution services: it contains the list of the Artifact Resolution Services to send request:
- Location: The URL or Web address for the endpoint.
- Binding: Input the binding for the endpoint
- Index: The priority ordering for the endpoint. It can also be used to identify the endpoint in requests.
- IsDefault: It indicates whether the endpoint is the default endpoint for this claims provider.
SAML 2.0 Protocol connection
We have new settings to support more values from the metadata:
- Other signing certificates: It contains the signing certificates from the metadata. These are used by Safewhere*Identify to verify signatures of messages which the Service Provider sends to Identify.
- Find value: The value of the attribute that is used by Safewhere*Identify to search for the certificate, e.g. its subject or thumbprint.
- Get certificates button: Allow users to select a new certificate.
- Find type: Specifies which certificate attribute that is used to match against the find value. A common way to locate a certificate is to search for its subject distinguished name or its thumbprint. The protocol connection will use the first certificate that matches the specified search criteria. Possible values are: FindByThumbprint, FindBySubjectName, FindBySubjectDistinguishedName, FindByIssuerName, FindByIssuerDistinguishedName, FindBySerialNumber, FindByTimeValid, FindByTimeNotYetValid, FindByTimeExpired, FindByTemplateName, FindByApplicationPolicy, FindByCertificatePolicy, FindByExtension, FindByKeyUsage, FindBySubjectKeyIdentifier.
- Store location: The location of the certificate store to use. Possible values are: CurrentUser, LocalMachine
- Store location name: Specifies which certificate store the certificate is placed in. Possible values are: My, TrustedPeople.
- In store?: This is a computed field which indicates if the certificate can be found based on what the user specified for the other signing certificate elements. The value is updated upon refresh of the page, so if you want to check if your values where correct, you should save the connection and see if the checkmark is ticked.
- Keyname: This specifies the keyname of the certificate.
- Other encryption certificates: It contains all the encryption certificates from the metadata. These are used by Safewhere*Identify to encrypt the messages which the Identity sends to the Service Provider.
- Find value: The value of the attribute that is used by Safewhere*Identify to search for the certificate, e.g. its subject or thumbprint.
- Get certificates button: Allow users to select a new certificate.
- Find type: Specifies which certificate attribute that is used to match against the find value. A common way to locate a certificate is to search for its subject distinguished name or its thumbprint. The protocol connection will use the first certificate that matches the specified search criteria. Possible values are: FindByThumbprint, FindBySubjectName, FindBySubjectDistinguishedName, FindByIssuerName, FindByIssuerDistinguishedName, FindBySerialNumber, FindByTimeValid, FindByTimeNotYetValid, FindByTimeExpired, FindByTemplateName, FindByApplicationPolicy, FindByCertificatePolicy, FindByExtension, FindByKeyUsage, FindBySubjectKeyIdentifier.
- Store location: The location of the certificate store to use. Possible values are: CurrentUser, LocalMachine
- Store location name: Specifies which certificate store the certificate is placed in. Possible values are: My, TrustedPeople.
- In store?: This is a computed field which indicates if the certificate can be found based on what the user specified for the other encryption certificate elements. The value is updated upon refresh of the page, so if you want to check if your values where correct, you should save the connection and see if the checkmark is ticked.
- Keyname: This specifies the keyname of the certificate.
- Single log off service:
- Binding: The binding that Safewhere*Identify should use to receive log off requests: “urn:oasis:names:tc:SAML:2.0:bindings:SOAP”, “urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect”, “urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST”, “urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact” .
- Location: The endpoint to which Safewhere*Identify should send log off requests via the above input binding.
- Response location: The endpoint to which Safewhere*Identify should send responses for log off requests via the above input binding.

- Artifact resolution services: it contains the list of the Artifact Resolution Services that Identify uses to resolve message from artifacts:
- Location: The URL or Web address for the endpoint.
- Binding: Input the binding for the endpoint
- Index: The priority ordering for the endpoint. It can also be used to identify the endpoint in requests.
- IsDefault: It indicates whether the endpoint is the default endpoint for this claims provider.
- Assertion consumer service: It contains the list of the Assertion consumer services:
- Location: The URL or Web address for the endpoint to which Safewhere*Identify should send sign on responses
- Binding: Input the binding for the endpoint which uses to send sign on responses to the involved RP
- Index: The priority ordering for the endpoint.
- IsDefault: It indicates whether the endpoint is the default endpoint.
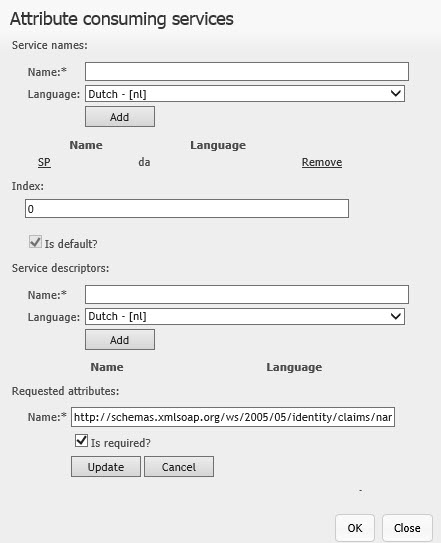
- Attribute consuming services: It contains the list of the Attribute consuming services:
- Name: The attribute consuming service name
- Index: The priority ordering for the attribute consuming service.
- IsDefault: It indicates whether the attribute consuming service is the default one or not.
Note: Each Attribute consuming service MUST contain exactly one attribute with the same name as ServiceID