Introduction
Safewhere’s SAML 2.0 for WIF component delivers a full implementation of the Security Assertion Markup Language (SAML) 2.0 protocol on the Windows Identity Foundation (WIF) enabling developers of ASP.NET applications to connect directly into SAML 2.0 federations. Our new component, SAML2.0 for WIF, allows you to leverage all the benefits of WIF, while still being able to participate directly in SAML 2.0 protocols. More information about the topic can be found here.
This article will guide you to control the binding that SAML2WIF uses to send AuthnRequest to an IdP, as well as the binding that it requires from the IdP‘s response. In order to register an IdP for SAML2WIF, add URL of the IdP to web.config file of SAML2WIF. By default, the file is located at C:\inetpub\Saml20ForWIF\WebSiteDemo\.
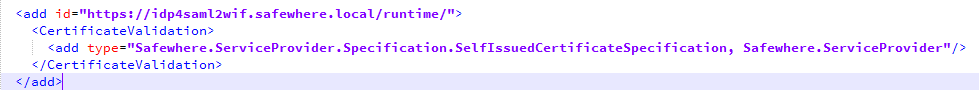
A typical IdP section in web.config looks like this
In scenario SAML2WIF-> IdP, when user click link of IdP from SAML2WIF, an AuthnRequest will be sent from SAML2WIF to IdP. In order to control the binding that SAML2WIF uses to send AuthnRequest to an IdP as well as the binding that SAML2WIF wants the IdP to response to it (AssertionConsumerServiceUrl or AssertionConsummerServiceIndex), add <SSO…></SSO> element to the aforementioned web.config file.
|
1 2 3 4 5 6 7 8 9 |
<add id="https://idp4saml2wif.safewhere.local/runtime/"> <CertificateValidation> <add type="Safewhere.ServiceProvider.Specification.SelfIssuedCertificateSpecification, Safewhere.ServiceProvider"/> </CertificateValidation> <SSO url="https://idp4saml2wif.safewhere.local/runtime/saml2/issue.idp" binding="POST" forceProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" forceAssertionConsumerServiceUrl="https://spdemo.safewhere.local/" forceAssertionConsumerServiceIndex="0"></SSO> </add> |
Explain:
- binding=”POST”: option tells SAML2WIF that it must use POST binding to send AuthnRequest to an IdP
- forceProtocolBinding: tells SAML2WIF to set the AuthnRequest.ProtocolBinding attribute to the configured value
- forceAssertionConsumerServiceUrl: tells SAML2WIF to set the AuthnRequest.AssertionConsumerServiceUrl attribute to the configured value
- forceAssertionConsumerServiceIndex: tells SAML2WIF to set the AuthnRequest.AssertionConsumerServiceIndex attribute to the configured value.
(Explanation about those settings can be found at: http://docs.oasis-open.org/security/saml/v2.0/saml-core-2.0-os.pdf from line 2051.)
Setting
– Open web.config of the SAML2WIF
– Add <SSO…></SSO> element as (a) or (b) pictures
(a)
|
1 2 3 4 5 6 7 8 |
<add id="https://idp4saml2wif.safewhere.local/runtime/"> <CertificateValidation> <add type="Safewhere.ServiceProvider.Specification.SelfIssuedCertificateSpecification, Safewhere.ServiceProvider"/> </CertificateValidation> <SSO url="https://idp4saml2wif.safewhere.local/runtime/saml2/issue.idp" binding="POST" forceProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" forceAssertionConsumerServiceUrl="https://spdemo.safewhere.local/"></SSO> </add> |
(b)
|
1 2 3 4 5 6 7 |
<add id="https://idp4saml2wif.safewhere.local/runtime/"> <CertificateValidation> <add type="Safewhere.ServiceProvider.Specification.SelfIssuedCertificateSpecification, Safewhere.ServiceProvider"/> </CertificateValidation> <SSO url="https://idp4saml2wif.safewhere.local/runtime/saml2/issue.idp" binding="POST" forceAssertionConsumerServiceIndex="0"></SSO> </add> |
– Restart IIS
– Start the scenario: SAML2WIF -> idp4saml2wif.safewhere.local
Verify
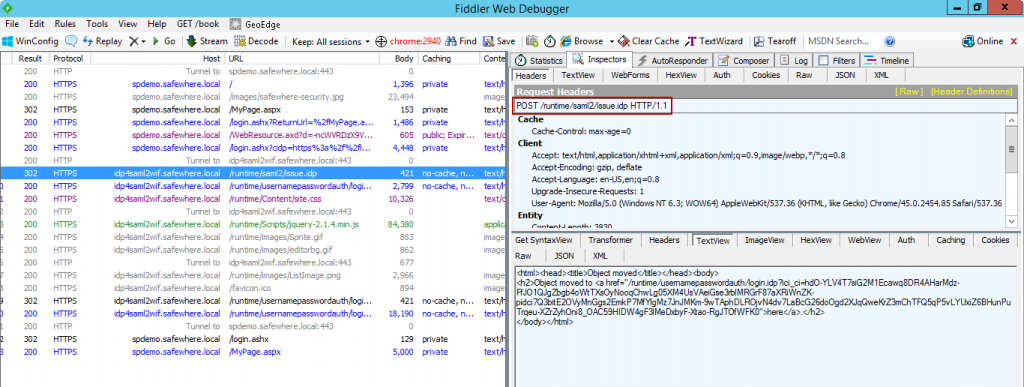
– Using Fiddler to track the SAML2WIF
– Confirm the “POST” method as below picture:
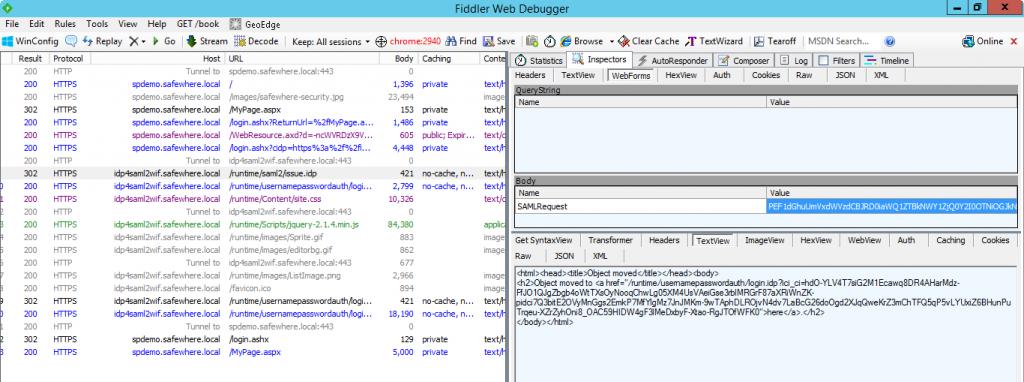
– Confirm the contain of SAML2 request: get content of SAML2 Request and decode it.
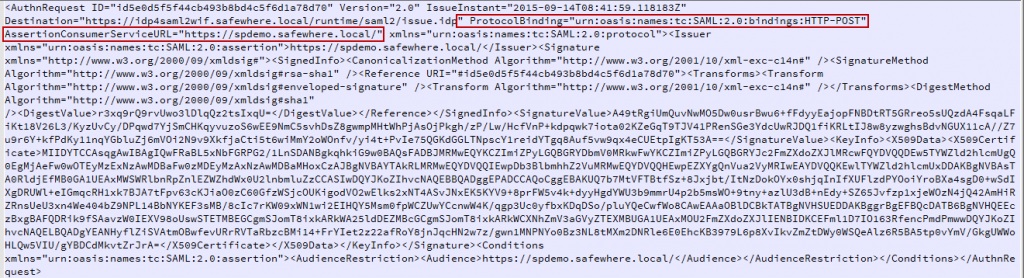
If using the config as (a) picture, content of SAML2 request after decoding like as below
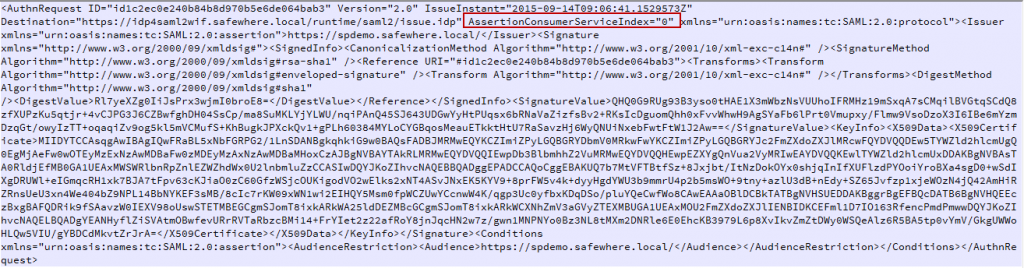
If using the config as (b) picture, content of SAML2 request after decoding like as below
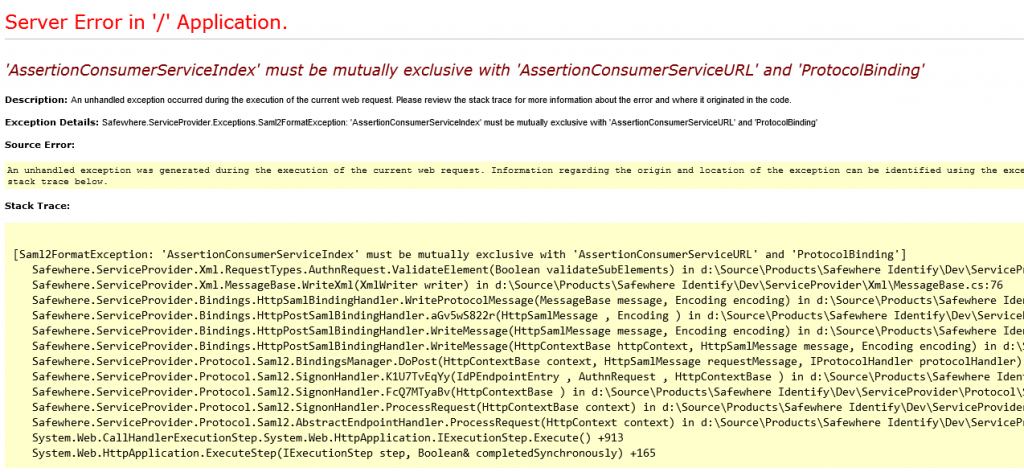
Note: the forceAssertionConsumerServiceIndex is mutually exclusive with the forceProtocolBinding and forceProtocolBinding attributes.In case you put all of these 3 parameters on <SSO> section like this:
The exception will be thrown: