The following article describes the process for connecting AD FS 2.0 to Safewhere*Identify. It is recommended that you read the following document before starting:
- Saml2Wif installation guideline (https://docs.google.com/document/d/1y5D0x4UNSAwxRP_9BBEUnhfBG7PDfX-t3AW4cvWcCIA/edit ). Please take special notice on all the powershell information in this document.
- Microsoft’s AD FS 2.0 installation guideline.
Saml2 Protocol Connections
The following example is in the context that ADFS (fed.safewhere.local) is a RP for identify1 (identify1.safewhere.local) using Saml2 protocol.
ADFS Configuration
- Add a Claims Provider Using Saml2 Metadata URL: https://identify1.safewhere.local/runtime/saml2/metadata.idp
- Create some claims rules as section Claim settings
- Change AD FS 2.0 Signature Algorithm to use the Secure Hash Algorithm 1 (SHA-1): right-click > Properties > On the Advanced tab, in the Secure hash algorithm list, select SHA-1,and then click OK.
- Using Windows Powershell to remove the Revocation Check when using self-certificates
- add-pssnapin microsoft.adfs.powershell
- set-ADFSClaimsProviderTrust -targetname “Claims_Provider_Name” -SigningCertificateRevocationCheck None
- set-ADFSClaimsProviderTrust -targetname “Claims_Provider_Name” -EncryptionCertificateRevocationCheck None
- Set-ADFSClaimsProviderTrust -targetname “Claims_Provider_Name” -SignedSamlRequestsRequired $True (This setting is used to resolve the error “Value cannot be null. Parameter name: signature” as ADFS did not sign the login message before passing through Identify)
Identify Configuration
- Go to Connections tab and create a Saml2 protocol connection, check enable
- Go back to the connection list, open the upload metadata form and point to https://fed.safewhere.local/FederationMetadata/2007-06/FederationMetadata.xml
- Then, we need to modify some fields in other to work with ADFS (they were considered as issues and will be fixed later – we just do some workaround to make this scenario work) – Go back to the connection list, select the Salm2 connection to edit
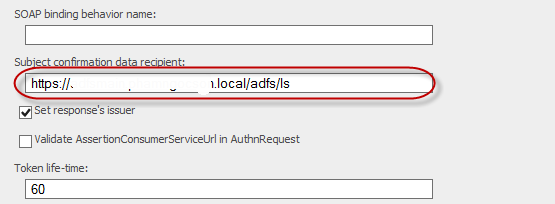
- Subject confirmation data recipient:* edit to https://fed.safewhere.local/adfs/ls/ instead of http://fed.safewhere.local/adfs/services/trust
- Enable Set response’s issuer
WS-Federation Protocol Connections
The following example is in the context that ADFS (fed.safewhere.local) is a RP for identify1 (identify1.safewhere.local) using WS Federation protocol.
ADFS Configuration
- Add a Claims Provider Using Federation Metadata URL: https://identify1.safewhere.local/runtime/FederationMetadata/2007-06/FederationMetadata.xml
- Create some claims rules as section Claim settings
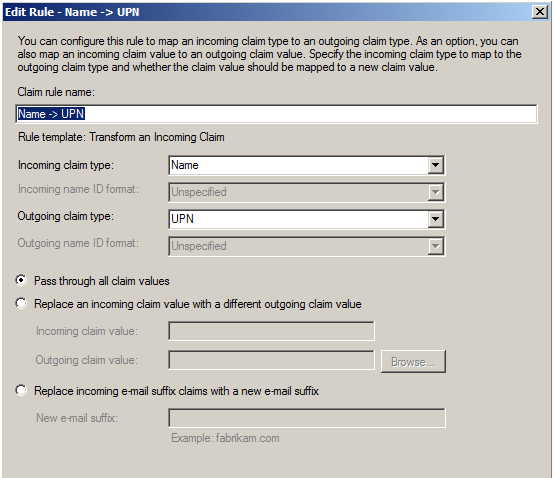
- In this case, a Name pass through rule needs to be created to pass reponse from Identify Idp to Identify*Admin SP
- Change AD FS 2.0 Signature Algorithm to use the Secure Hash Algorithm 1 (SHA-1): right-click > Properties > On the Advanced tab, in the Secure hash algorithm list, select SHA-1,and then click OK.
- Using Windows Powershell to remove the Revocation Check when using self-certificates
- add-pssnapin microsoft.adfs.powershell
- set-ADFSClaimsProviderTrust -targetname “Claims_Provider_Name” -SigningCertificateRevocationCheck None
- set-ADFSClaimsProviderTrust -targetname “Claims_Provider_Name” -EncryptionCertificateRevocationCheck None
Identify Configuration
- Go to Connections tab and create a Federation protocol connection, check enable
- Go back to the connection list, open the upload metadata form and point to https://fed.safewhere.local/FederationMetadata/2007-06/FederationMetadata.xml
Claim settings
A typical set up when Identify is an IdP of AD FS 2.0 is:
SP → AD FS 2.0 → Identify
So in term of claims issuance and transformation, we have two steps:
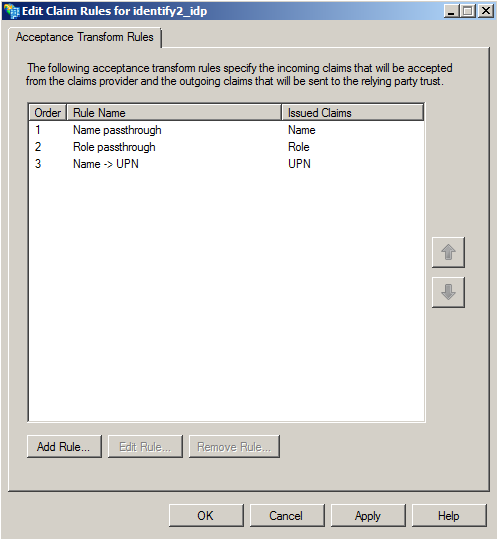
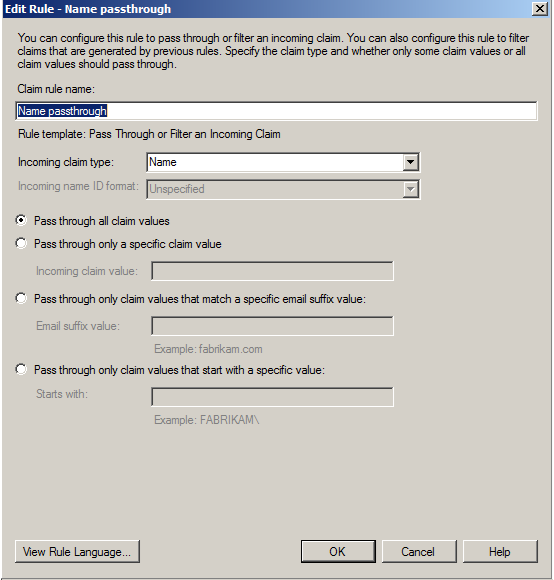
- Identify → AD FS 2.0: AD FS 2.0 applies some transformation rules to the incoming claims. For example, a name passthrough rule will allow name claim from Identify to pass through to the outgoing connection.
- AD FS 2.0 → SP: similar to how one connects Identify to AD FS 2.0
The minimal set of transformation rules to apply to claims from Identify which works is:
Troubleshooting
1) You get the error like the image below:
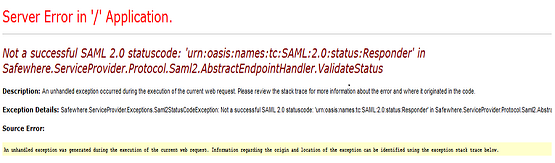
and the exception in ADFS event viewer is:
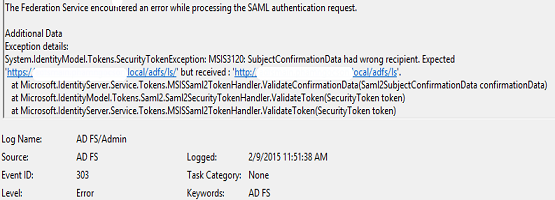
Solution: Please check the protocol that you are using for “Subject confirmation data recipient in” in Saml2 Protocol Connections setting. Make sure it is https, NOT http.