Introduction
To verify Identify against the OpenID Connect, we can use the sample OIDCClient to demonstrate that Identify does support SLO/SSO for OpenId Connect
How to setup OIDCClient
1. Open the IIS and setup this sample as the application for the site on IIS
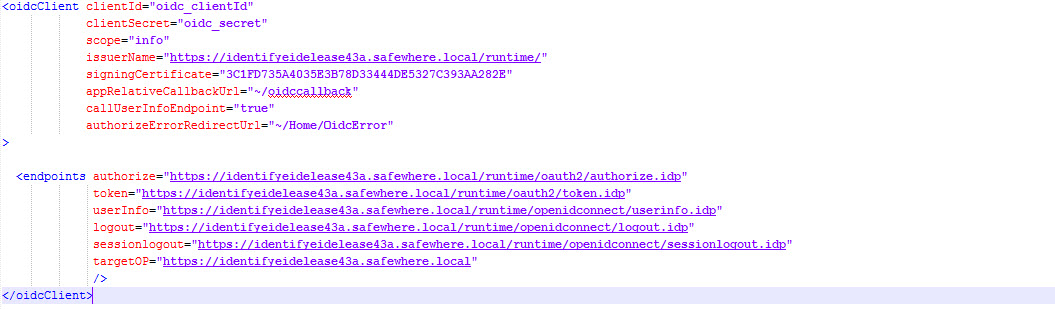
2. At its source folder, we open the oidc.config then update the URIs on the file by your tenant URI and the signingCertificate value by your tenant signing like below:
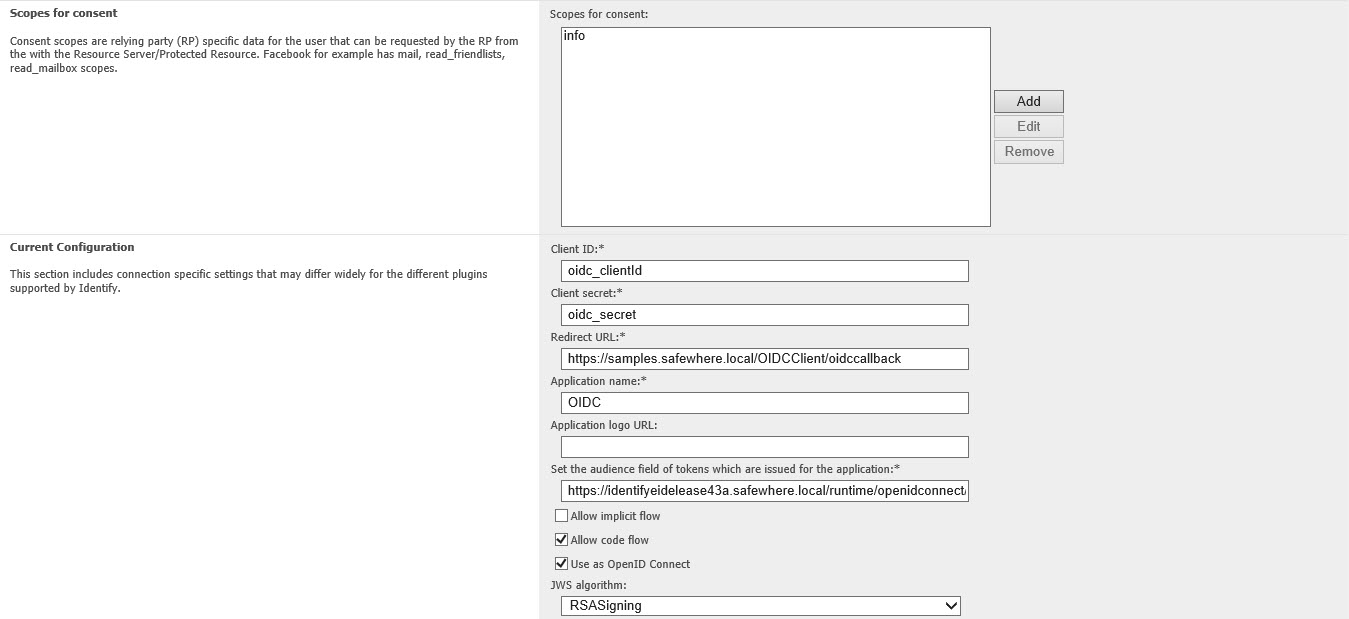
3. Go to the connection list on Admin, we add the new Oauth 2.0 protocol connection where we will setup like below:
+ Scope: we will add the scope “info” as the key “scope” ‘s value at the above oidc.config
+ Client ID: we will add the value on the key “clientId” at the above oidc.config
+ Client secret: we will add the value on the key “clientSecret” at the above oidc.config
+ Redirect URL: we will add the value following the URI of the OIDCClient, e.g in this sample: https://samples.safewhere.local/OIDCClient/oidccallback
+ Application name: input the name for the OIDCClient
+ Set the audience field of tokens which are issued for the application: we will input the userInfo endpoint of the OpenIDConnect: https://#Identifydomain/runtime/openidconnect/userinfo.idp
+ Allow implicit flow: we set it False
+ Allow code flow: we set it True
+ Use as OpenID Connect: we set it True
+ JWS alorithm: we choose “RSASigning”
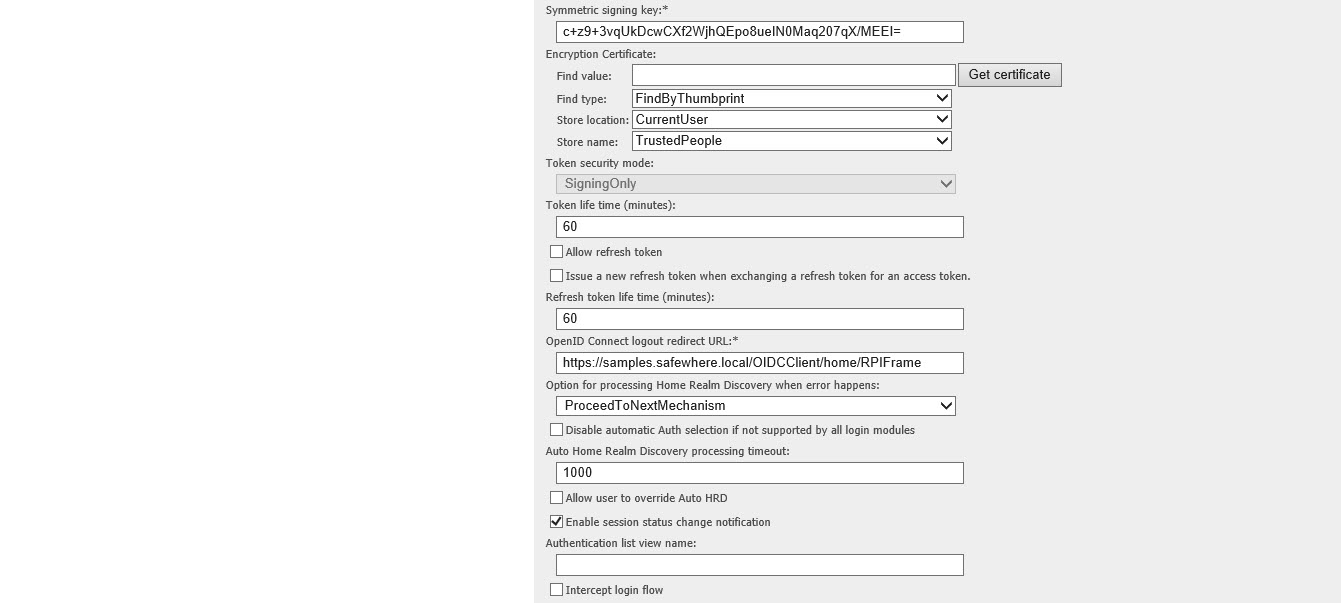
+ Symmetric signing key: we click the below button “Open auto-generated HMAC” to generate its value
+ OpenID Connect logout redirect URL: we will add the value following the URI of the OIDCClient, e.g in this sample: https://samples.safewhere.local/OIDCClient/home/RPIFrame
Here is the demo for OIDCClient login when it’s setup successfully: http://screencast.com/t/CPQmUfc4Fk