SAML 2.0 is a huge specification with numerous options from which organizations build their own derived specifications. Each derived specification usually has its own ideas about what are required, what are not, and what must be validated.
In order to cope with those specific requirements, Safewhere*Identify now introduces the “Profile” concept. When a specific profile is selected for a tenant or a connection, Identify applies profile-specific processing code for it. The two supported profiles in 4.3 are OIOSAML and eHerkenning. As a side note, choosing “OIOSAML” profile will not be different from choosing the “None” profile because most of the default behaviors actually follow OIOSAML specification
You can configure it in the System setup page:
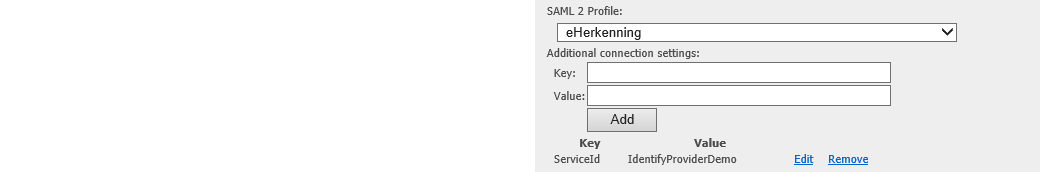
This is how it looks like in the SAML 2.0 authentication connection page:
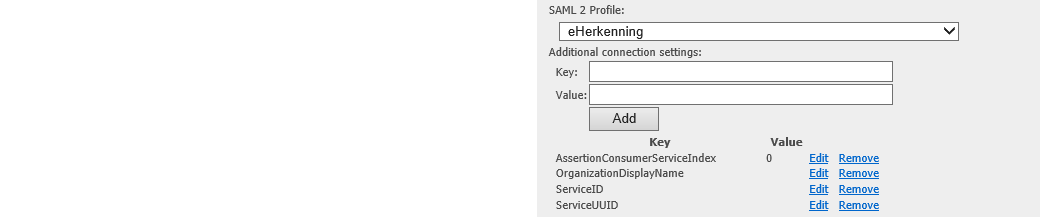
Similarly, SAML 2.0 protocol connection has the same setting:
Note: when the “Profile” setting is set to “eHerkenning” for a SAML 2.0 protocol connection, the following keys are added by default:
- AssertionConsumerServiceIndex: Default value is 0
- OrganizationDisplayName: Default value is Empty
- ServiceID: Default value is Empty
- ServiceUUID: Default value is Empty
Those settings are necessary for the flow “DV => HM => AD” so thus must be configured accordingly.