Introduction
In addition to REST API supports for provisioning SAML 2.0 and WSFed connections in previous versions, Identify now also has support all other connection types as well as full support for all connections’ settings that you can find in Identify*Admin. This topic will describe all the new features briefly. Please refer to our REST API documentation and sample code on Github for more details (https://github.com/Safewhere/Safewhere-Identify-samples).
New settings support for SAML 2.0 and WSFed connections
We support the new properties in the json model REST API for Saml2 Pro and Saml2 Authen:
1. SAML 2.0 protocol connection:
a. Home Realm Discovery rules:
This is new to REST API for SAML 2.0 and WSFed connections and is supported for all other connection types too. The HRD rules are displayed on Identify*Admin as in the screenshot below:

Which are represented in Json format for REST API as follow:
“appliedHomeRealmDiscoveryRules”: [
“Whr parameter”,
“Persistent cookie”,
“Show tailored IDPs list from CDC”,
“Common domain cookie”,
“Ip-based HRD”,
“Auto HRD”,
“Identify-initiated common domain cookie”,
]
b. Evaluate requested authentication context:
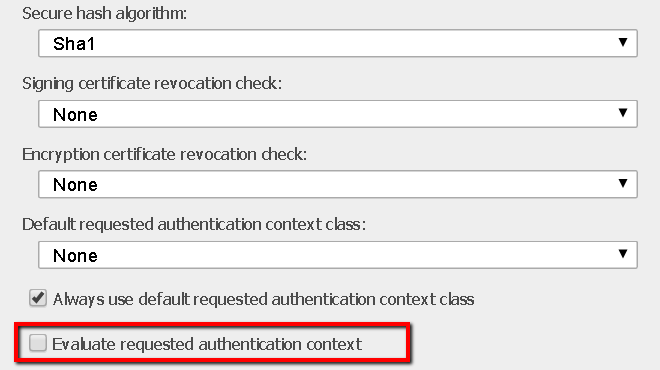
The “Evaluate requested authentication context” setting is for SAML 2.0 protocol connection only. Its corresponding JSON property is “evaluateRequestedAuthenticationContext” whose default value is false.
2. Saml2 Authentication connection:
a. Opt out from persistent cookies
- On UI:
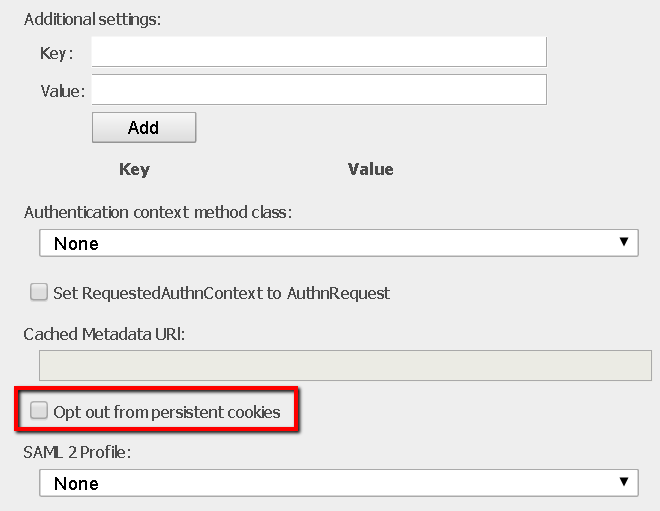
The “Opt out from persistent cookies” setting is for SAML 2.0 authentication connection only. Its corresponding JSON property is “optOutOfPersistentCookies” whose default value is false.
Support multiple configuration sections and activation time for all connections
In version 5.0, each connection has multiple configurations, and each configuration has an activation time. An activation time is a period during that a connection’s configuration is active.
Here is example:
{
“doNotRegisterUsers”: false,
“allowUserAutoRegistration”: false,
“secondFactorAuthenticationConnectionName”: “”,
“twoFactorIdentitiesCondition”: “None”,
“bearingClaimType”: “http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name”,
“organizationNameOfAutoCreatedUsers”: null,
“userTemplateClaims”: [],
“enabled”: true,
“accessOrganizationName”: “Root”,
“dependencyConnectionNames”: [],
“claimTransformations”: [],
“issuesRoles”: true,
“allowedIpAddresses”:null,
“configuration”: null,
“configurations”: [
{
“entityIdentifier”: “https://identify-demo2.safewhere.local/runtime/”,
“defaultNameIdFormat”: “urn:oasis:names:tc:SAML:2.0:nameid-format:persistent”,
“signingCertificate”: {
“isSelfSigned”: false,
“revocationCheck”: “None”,
“storeReference”: {
“storeName”: “TrustedPeople”,
“storeLocation”: “CurrentUser”
},
“findCriterion”: {
“findType”: “FindByThumbprint”,
“value”: “3C1FD735A4035E3B78D33444DE5327C393AA282E”
}
},
“signingCertificateIsInStore”: true,
“encryptionCertificate”: {
“isSelfSigned”: false,
“revocationCheck”: “None”,
“storeReference”: {
“storeName”: “TrustedPeople”,
“storeLocation”: “CurrentUser”
},
“findCriterion”: {
“findType”: “FindByThumbprint”,
“value”: “3C1FD735A4035E3B78D33444DE5327C393AA282E”
}
},
“encryptionCertificateIsInStore”: true,
“singleLogOffService”: {
“binding”: “urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect”,
“location”: “https://identify-demo2.safewhere.local/runtime/saml2/issue.idp”,
“responseLocation”: “https://identify-demo2.safewhere.local/runtime/saml2/signoff.idp”
},
“postBindingSingleLogOffService”: {
“binding”: “urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST”,
“location”: “https://identify-demo2.safewhere.local/runtime/saml2/issue.idp”,
“responseLocation”: “https://identify-demo2.safewhere.local/runtime/saml2/signoff.idp”
},
“soapBindingSingleLogOffService”: {
“binding”: “urn:oasis:names:tc:SAML:2.0:bindings:SOAP”,
“location”: “https://identify-demo2.safewhere.local/runtime/services/signoff/saml2/soap”,
“responseLocation”: “https://identify-demo2.safewhere.local/runtime/services/signoff/saml2/soap”
},
“soapBindingBindingName”: “”,
“soapBindingBehaviorName”: “”,
“signingAlgorithm”: “Sha1″,
“metadataLocation”: “https://identify-demo2.safewhere.local/runtime/saml2/metadata.idp”,
“singleSignOnService”: {
“binding”: “urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect”,
“location”: “https://identify-demo2.safewhere.local/runtime/saml2/issue.idp”,
“responseLocation”: “https://identify-demo2.safewhere.local/runtime/saml2/issue.idp”
},
“singleSignOnArtifactResolution”: {
“binding”: “urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect”,
“location”: “http://localhost/”,
“responseLocation”: “http://localhost/”
},
“alwaysOverrideWithDefaultNameIdFormat”: false,
“useIfNoNameIdFormatIsSpecified”: false,
“setNameIdPolicyToThatOfAuthnRequest”: false,
“setAuthenticationRequestAssertionConsumerServiceUrl”: false,
“validateSubjectConfirmationDataRecipient”: false,
“rejectedAuthenticationContextMethodClasses”: “”,
“alwaysOverrideSessionNotOnOrAfterWithFederatedSessionLifetime”: true,
“setRequestedAuthnContextToAuthnRequest”: false,
“authenticationContextMethodClassMapping”: [],
“encryptionCertificateRevocationCheck”: “None”,
“signingCertificateRevocationCheck”: “None”,
“samlProfiles”: “None”,
“artifactBindingSingleLogOffService”: {
“binding”: “urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact”,
“location”: “https://identify-demo2.safewhere.local/runtime/saml2/artifact.idp”,
“responseLocation”: “https://identify-demo2.safewhere.local/runtime/saml2/artifact.idp”
},
“otherEncryptionCertificates”: [
{
“isSelfSigned”: false,
“revocationCheck”: “None”,
“storeReference”: {
“storeName”: “TrustedPeople”,
“storeLocation”: “CurrentUser”
},
“findCriterion”: {
“findType”: “FindByThumbprint”,
“value”: “3C1FD735A4035E3B78D33444DE5327C393AA282E”
}
}
],
“otherSigningCertificates”: [
{
“isSelfSigned”: false,
“revocationCheck”: “None”,
“storeReference”: {
“storeName”: “TrustedPeople”,
“storeLocation”: “CurrentUser”
},
“findCriterion”: {
“findType”: “FindByThumbprint”,
“value”: “3C1FD735A4035E3B78D33444DE5327C393AA282E”
}
}
],
“artifactResolutionServices”: [
{
“binding”: “urn:oasis:names:tc:SAML:2.0:bindings:SOAP”,
“location”: “https://identify-demo2.safewhere.local/runtime/services/artifact/saml2/soap”,
“index”: 0,
“isDefault”: true
}
],
“connectionAdditionalSettings”: [],
“soapBindingCustomSetting”: “”,
“soapBehaviorCustomSetting”: “”,
“setBootstrapTokenForClaimsPrincipal”: false,
“authnRequestCustomizationScript”: “”,
“ignoredBySecondFactorRolesClaimType”: “”,
“ignoredBySecondFactorRoles”: “”,
“ignoreRolesCheck”: false,
“useAsSecondFactorOnly”: false,
“federatedSessionLifetime”: 480,
“enabledForMobileUse”: true,
“ipBaseHomeRealmDiscoveryFilter”: “”,
“supportsAutomaticAuthSelection”: false,
“authenticationContextMethodClass”: “None”,
“interceptorService”: {
“useInterceptor”: false,
“interceptorViewName”: “”,
“interceptorService”: “None”,
“interceptorDependencyService”: “None”,
“additionalSettings”: []
},
“authLoginStatusChecker”: “~\\AuthChecker\\Saml2PreAuthStatusChecker.js”,
“optOutOfPersistentCookies”: false,
“showReturnToLoginSelectorLink”: false,
“customAuthenticationView”: “”,
“configurationId”: “e4375876-222c-464c-b977-52a9659aaf4e”,
“configurationType”: “Saml2Authentication”,
“activationTime”: {
“startTime”: “0001-01-01T00:00:00Z”,
“endTime”: “9999-12-31T23:59:59Z”
}
},
{
“entityIdentifier”: “https://identify-demo2.safewhere.local/runtime/”,
“defaultNameIdFormat”: “urn:oasis:names:tc:SAML:2.0:nameid-format:persistent”,
“signingCertificate”: …
}
}
],
“pluginType”: “Saml20″,
“connectionName”: “SAMl20 Authentication 2″,
“organizationName”: “Root”,
“connectionType”: “Authentication”,
“metadataReference”: null,
“autoSetAllDependencies”: false,
“externalId”: null,
“meta”: {
“created”: “0001-01-01T00:00:00″,
“lastModified”: “0001-01-01T00:00:00″,
“location”: “”,
“version”: null,
“attributes”: null
},
“name”: “SAMl20 Authentication 2″,
“description”: null,
“endpoint”: “/admin/api/rest/v2/Connections”,
“schema”: “urn:scim:schemas:core:2.0:Connection”,
“schemaExtensions”: null,
“schemaExtensionsDetail”: null
}
In which:
- configurations.ID is unique in a conection. If you don’t set it when POST/PUT a connection, the system will generate a GUI value for it.
- configurations.activationTime is not required for POST/PUT. If you don’t set it, the default values (Min date for startTime and Max date for endTime) will be used.
- When a connection has multiple configuration sections, their activation time periods must not overlap.
- All configuration sections of a connection must have the same EntityIdentifier. They can have different ExtraEntityIds though.
Add/remove a list of Claims Transformations (CTs) to a connection
- Add a list of CTs to a connection
- API: /admin/api/rest/v2/connections/transformations
- Method: PUT
- Content-type: application/json
- Authorization: Oauth2 token
- Json model:
{
“ClaimTransformations”: [
“string”
],
“ConnectionName”: “string”
}
This api allow us to add a list of CTs to a connection. If the connection currently has no claims transformations, Identify will add the CTs to the connection. On the other hand, all new CTs will be merged with existing CTs. For example, if a connection already has 3 CTs [A, C, E] and we PUT [D, C, A], the result will be [A, C, E, D].
- Remove a list of CT from a connection
- API: /admin/api/rest/v2/connections/transformations
- Method: DELETE
- Content-type: application/json
- Authorization: Oauth2 token
- Json model:
{
“ClaimTransformations”: [
“string”
],
“ConnectionName”: “string”
}
