Introduction
Safewhere*Identify supports extensive logging which is virtually sufficient for all the needs for monitoring, reporting, and debugging. To make the logging functionality even better, Identify 5.0 allows for controlling what log types should be enabled as well as log levels via Identify*Admin interface. This is a big improvement in comparison to prior versions when you had to touch configuration files to change logging settings.
Types of logs
| Name | Abbreviation | Description |
| System log | SYS | Contains all warnings, errors and debug logs. As you can see in examples below, all the new log types have richer information than the legacy audit log. |
| Audit log | N/A | Audit log is stored in the IdentifyAudit SQL database. Identify has support for this log type for many versions. This log type includes:● All changes made to Identify’s data models, e.g. User, Connection. ● Content of SAML 2.0 and WSFed messages (aka user requests). ● Token issuances. |
| Security log | SEC | Security log contains data about:- SAML 2.0 messages. – Validation results for certificates which are used by those messages. – We will support security log for other plugins in 5.1.A plus point of security log is that SAML 2.0 messages are logged in plain text even if original messages are encrypted. |
| Billing log | BILL | Collects information relevant to settle billing requirements such as where a request comes from, where it is sent to, its size, and time used to process it. |
| Revision log | REV | Collects information about how the system is used – When REST API is called. – Create/Update/Delete resources via Admin UI – User requests |
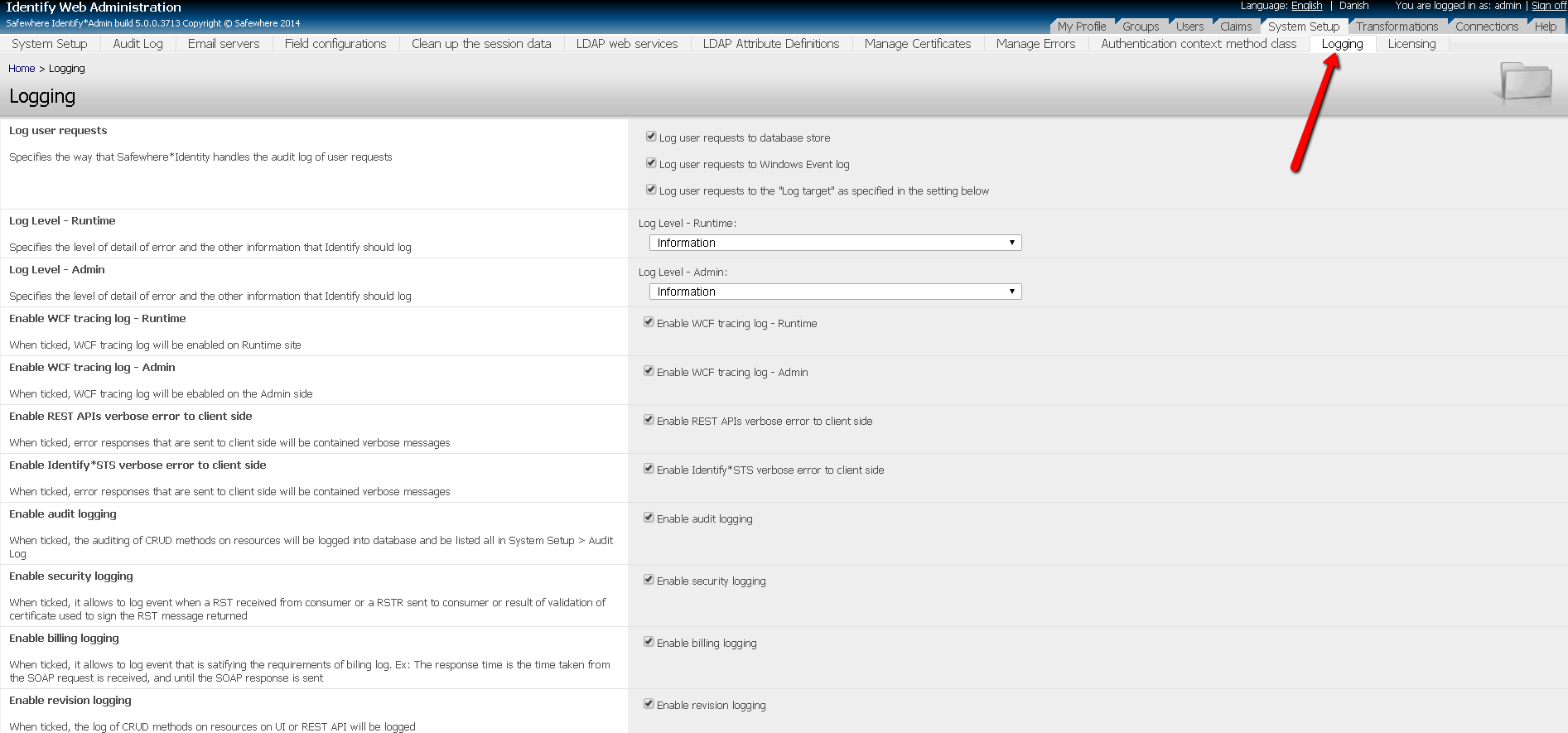
Logging setting in Identify*Admin
- Logging settings can be found in System setup -> Logging tab. Below are options you can set:
- Log user requests to database store: check to enable user requests logs written to database. Recommended setting for production: it depends on whether your installation needs this type of log and where you want to log to.
- Log user requests to Windows Event log: check to enable user requests logs written to Windows Security event. Recommended setting for production: it depends on whether your installation needs this type of log and where you want to log to.
- Log user requests to the “Log target” as specified in the setting below: check to enable user requests logs written to store which is specified by the Log Target setting below. Recommended setting for production: it depends on whether your installation needs this type of log and where you want to log to.
- Log Level – Runtime: specify the level of security log, billing log, and revision log for Identify*Runtime. Supported value are Verbose, Information, Error or Off. Recommended setting for production: Information. When you don’t need this log type, Error should be used.
- Log Level – Admin: specify the level of security log, billing log, and revision log for Identify*Admin. Supported value are Verbose, Information, Error or Off. Recommended setting for production: Information. When you don’t need this log type, Error should be used.
- Enable WCF tracing log – Runtime: check to enable WCF logging for Identify*Runtime activities. Recommended setting for production: unchecked
- Enable WCF tracing log – Admin: check to enable WCF logging for Identify*Admin activities. Recommended setting for production: unchecked
- Enable REST APIs verbose error to client side: check to enable including verbose error in message sent back to REST client in case error occurs. Recommended setting for production: unchecked
- Enable Identify*STS verbose error to client side: returns verbose error messages for unhandled errors, mostly errors happening when Identify is verifying access tokens. Recommended setting for production: unchecked
- Enable audit logging: control whether Identify should do legacy audit log. Recommended setting for production: checked if your installation requires that audit data must go into SQL database.
- Enable security logging: control whether Identify should do security log. Recommended setting for production: checked.
- Enable billing logging: control whether Identify should do billing log. Recommended setting for production: checked.
- Enable revision logging: control whether Identify should do revision log. Recommended setting for production: checked.
- Log target: specify where logs is written to, currently Windows event and text file are supported. Recommended setting for production: either Text file or Windows Event Log.
- Log folder: The default folder for logging is: C:\Program Files\Safewhere\Identify\Tenants\your_tenant\Logs . You can change the log folder by editing it in the web.config files. We will add support for configurable log folder in a future version.
Log examples
Each log entry is in json format.
System log
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 |
{ "LogLevel": "DEBUG", "Type": "SYS", "LogMessage": "Create: RequestEnteredPassiveContextRestorationStepObserver.Restore: IsSignOnRequest", "EventId": "9999", "LogId": "a146a46f-275e-47f7-af0b-608b408a1c4f", "HttpRequestParameters": { "QueryString": { "wa": "wsignin1.0", "wtrealm": "https://identify-demo.safewhere.local/admin/", "wctx": "rm=0&id=passive&ru=%2fadmin%2f", "wct": "2016-07-27T16:00:54Z" }, "Path": "/runtime/WSFederation/WSFederation.idp", "Method": "GET" }, "Timestamp": "2016-07-27T16:01:09.6232108Z", "IPAddress": "127.0.0.1", "MachineName": "WIN2K12R2", "UserId": "00000000-0000-0000-0000-000000000000" } |
| Name | Description |
| LogLevel | Severity level, eligible values are DEBUG, INFO, WARNING, ERROR |
| Type | Log type, value must be SYS |
| LogMessage | More detail information about the event |
| EventId | Every log event has a unique event id. |
| LogId | Unique ID dynamically generated for every event |
| HttpRequestParameters | (Optional) The HTTP request parameters, consist of “QueryString”, “Path”, “Method”, and Forms parameters |
| Timestamp | Time event occurs |
| IPAddress | IP of the machine initiates the request |
| MachineName | Name of the machine initiates the request |
| UserId | Unique ID of the user that produced the request. For AuthnRequests we don’t have this. For Responses it’s the subject. For RST/RSTR it’s the subject |
Security log for SAML2
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
{ "Type": "SEC", "Component": "Passive", "Message": "...", "Action": "SamlProtocolActionResult - Passive issued an assertion to a user system", "EventId": "5521", "LogId": "57dc9e70-dc91-4ea0-9640-4b84b5fd6cd4", "HttpRequestParameters": { "QueryString": { "SAMLRequest": "lZHB..", "SigAlg": "http://www.w3.org/2001/04/xmldsig-more#rsa-sha256", "Signature": "U/7r.." }, "Path": "/runtime/saml2/issue.idp", "Referrer": "https://saml2wif.safewhere.org/", "Method": "GET" }, "Timestamp": "2016-07-27T16:02:06.0920064Z", "IPAddress": "127.0.0.1", "MachineName": "WIN2K12R2", "UserId": "00000000-0000-0000-0000-000000000000" } |
| Name | Description |
| Type | Log type, value must be SEC |
| Component | Must be “Passive” for SAML2 |
| Message | The whole Saml2 message |
| Action | Saml2 plugin actions |
| EventId | Every log event has a unique event id. |
| LogId | Unique ID dynamically generated for every event |
| HttpRequestParameters | The HTTP request parameters, consist of “QueryString”, “Path”, “Method”, and Forms parameters |
| Timestamp | Time event occurs |
| IPAddress | IP of the machine initiates the request |
| MachineName | Name of the machine initiates the request |
| UserId | Unique ID of the user that produced the request For AuthnRequests we don’t have this. For Responses it’s the subject. For RST/RSTR it’s the subject |
Billing log (BIL)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
{ "Type": "BIL", "Status": "200 OK", "ResponseTime": 7441, "ResponseSize": 421, "RequestSize": 194, "Operation": "/runtime/WSFederation/WSFederation.idp", "EventId": "7000", "LogId": "b2a622c5-cc71-40ed-9810-bfb88175d5f8", "HttpRequestParameters": { "QueryString": { "wa": "wsignin1.0", "wtrealm": "https://identify-demo.safewhere.local/admin/", "wctx": "rm=0&id=passive&ru=%2fadmin%2f", "wct": "2016-08-02T12:12:53Z" }, "Path": "/runtime/WSFederation/WSFederation.idp", "Method": "GET" }, "Timestamp": "2016-08-02T12:13:19.5421474Z", "IPAddress": "127.0.0.1", "MachineName": "WIN2K12R2", "UserId": "00000000-0000-0000-0000-000000000000" } |
| Name | Description |
| Type | Log type, value must be BIL |
| Status | Status of the request, ex: 200 OK |
| ResponseTime | Time taken from request was received to response was sent, measured in ms |
| ResponseSize | Size of the response in bytes |
| RequestSize | Size of the request in bytes |
| Operation | Name of the method or operation that was called |
| EventId | Every log event has a unique event id. |
| LogId | Unique ID dynamically generated for every event |
| HttpRequestParameters | The HTTP request parameters, consist of “QueryString”, “Path”, “Method”, and Forms parameters. |
| Timestamp | Time event occurs |
| IPAddress | IP of the machine initiates the request |
| MachineName | Name of the machine initiates the request |
| UserId | Unique ID of the user that produced the request For AuthnRequests we don’t have this. For Responses it’s the subject. For RST/RSTR it’s the subject |
Revision log (REV)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 |
{ "RevisionData": { "LocalTimestamp": "2016-08-02T16:22:32.8375957+07:00", "Id": 1765, "EventType": "InsertAuditAdminSiteAuthentication", "UtcTimestamp": "2016-08-02T09:22:32.8375957Z", "UserName": "admin", "ApplicationId": "https://identifydemo.safewhere.local/runtime/", "ContextId": "(unknown)", "AuditAdminSiteAuthentications": [ { "Id": 67, "AuditEventId": 1765, "ActionType": "SignOn" } ] }, "Type": "REV", "RevisionType": "InsertAuditAdminSiteAuthentication", "EventId": "20028", "LogId": "6077b8a4-4360-4bc3-a953-2de4b2104540", "HttpRequestParameters": { "Path": "/admin/", "Referrer": "https://identifydemo51.safewhere.local/runtime/usernamepasswordauth/login.idp?ici_ci=aal5YnBDfWXaLHwHX_xSjKmmYz45-IDUelnoZbnGeywN1lGhcDcGu6GGKHtvtx5Dadz5NIbLyvEkhO4OSOE-nM2xgStH-09K8yP54qhr81GOf5QNMwiaejk2Id3UBQyrRqev2MynKaFJ3gLwVsuhnoJMvogRDThVKCN6DTHksWAgM9dt6xVNxApSEb_gF5DB8w_kPyqxzyoMvmGIA-0jPhTxt07qMCNVE03fDpttDuE3oqmqJ1b6hrZO68MBkRmI0", "Method": "POST", "RequestContent": {} }, "Timestamp": "2016-08-02T09:22:32.8551019Z", "IPAddress": "127.0.0.1", "MachineName": "WIN2K12R2", "UserId": "00000000-0000-0000-0000-000000000000" } |
| Name | Description |
| RevisionData | Provisioning data |
| Type | Log type, value must be REV |
| EventId | Every log event has a unique event id. |
| LogId | Unique ID dynamically generated for every event |
| HttpRequestParameters | The HTTP request parameters, consist of “QueryString”, “Path”, “Method”, and Forms parameters |
| Timestamp | Time event occurs |
| IPAddress | IP of the machine initiates the request |
| MachineName | Name of the machine initiates the request |
| UserId | Unique ID of the user that produced the request For AuthnRequests we don’t have this. For Responses it’s the subject. For RST/RSTR it’s the subject |
Appendix A: List of Event IDs for System log (SYS)
| ID | Description |
| 97 | Web service communication error |
| 98 | Authentication connection not found in session error |
| 99 | Common logout error |
| 100 | Common runtime error |
| 101 | Connection resolution error |
| 102 | License error |
| 103 | Malformed request error |
| 104 | Path resolution error |
| 105 | Web service error |
| 106 | Audit user request error |
| 107 | Sending email error |
| 108 | Security error |
| 110 | Not supported exception |
| 111 | Configuration error |
| 120 | Text resource error |
| 130 | Database error |
| 140 | External claim transformation error |
| 141 | SQL claim transformation error |
| 142 | Regular expression condition parsing error |
| 143 | Invalid operation claim transformation error |
| 145 | Scripting claim transformation compilation error |
| 146 | Excluded pass through claim transformation error |
| 147 | Common claim transformation runtime log |
| 1440 | User account update claim transformation – Invalid claim value added error |
| 1441 | User account update claim transformation – Invalid bearing claim value added error |
| 1442 | User account update claim transformation – Invalid email claim value added error |
| 1443 | User account update claim transformation – Invalid update option error |
| 150 | Home Realm Discovery rules – Whr parameter error |
| 151 | Home Realm Discovery rules -Common domain cookie error |
| 152 | Home Realm Discovery rules -Common error |
| 153 | Home Realm Discovery rules – IP based error |
| 154 | Home Realm Discovery rules – Read cookie error |
| 160 | Authentication Session expired |
| 300 | Certificate error |
| 301 | Certificate revocation check error |
| 999 | Supplemental Data |
| 3011 | Saml2 authentication request validation error |
| 3012 | Saml2 authentication response validation error |
| 3013 | Saml2 faulty response sent |
| 3014 | Saml2 sign on error |
| 3015 | Saml2 Http message error |
| 3016 | Saml2 Relay State missing |
| 3017 | Saml2 artifact not exist or expired |
| 3040 | Saml2 unsuccessful logout response received error |
| 3050 | Saml2 service invalid protocol connection error |
| 3051 | Saml2 service invalid Uid attribute error |
| 3052 | Saml2 service invalid configuration error |
| 3053 | Saml2 service invalid request error |
| 3054 | Saml2 service data response error |
| 3112 | WS Federation security token validation error |
| 3114 | WS Federation faulty state |
| 3115 | WS Federation Protocol error |
| 3116 | WS Federation Wctx missing |
| 3310 | NemId – Common log on error |
| 3312 | NemId – Signature error |
| 3314 | NemId – Validation error |
| 3712 | Facebook – Response error |
| 3716 | Facebook – State code missing |
| 3812 | Twitter – Response error |
| 3816 | Twitter – State code missing |
| 3912 | Google – Response error |
| 3916 | Google – State code missing |
| 4011 | Device Based – Connection not found error |
| 4112 | LinkedIn – Response error |
| 4116 | LinkedIn – State code missing |
| 4212 | OpenId – Response error |
| 4216 | OpenId – State code missing |
| 4312 | LiveId – Response error |
| 4316 | LiveId – State code missing |
| 4410 | OTP – Common error |
| 4511 | UserName & Password – Update password error |
| 4512 | UserName & Password – Authentication session exist error |
| 4712 | Ldap Authentication – Session exist error |
| 4717 | Ldap reset password failed |
| 4810 | Generic Provider – CommonError |
| 4811 | Generic Provider – Could not load external provider error |
| 4812 | Generic Provider – Unhandled exception from external provider error |
| 4813 | Generic Provider – Name claim is empty or can not parse |
| 4910 | OAuth2 – Invalid authorization request |
| 4911 | OAuth2 – Invalid access token request |
| 4912 | OAuth2 – Invalid user information request |
| 4913 | OAuth2 – Invalid logout request |
| 5001 | STS – Configuration loading error |
| 5003 | STS – Invalid wstrust protocol connection found error |
| 5004 | STS – Client certificate validation failed error |
| 5005 | STS – Username credential validation failed error |
| 5020 | STS – Log information event |
| 5050 | STS – Unknown error |
| 5100 | REST – Service common error |
| 5102 | REST – Invalid request |
| 5120 | Spml common error |
| 5200 | Yubico Authentication – Common error |
| 5201 | Yubico Authentication – Response error |
| 6000 | OpenId Protocol – Invalid authentication request |
| 6001 | OpenId Protocol – Valid requested attribute not found |
| 8000 | System common error |
| 9999 | Debug event log |
| 9000 | Warning event log |
Appendix B: List of Event IDs for Saml2/ WSFed/ U&P/ NemID/ OTP/ Facebook/ Google/ Twitter/ LinkedIn/ Device-Base/ LiveId/ Ldap/ Yubico/ Generic Provider/ STS plugins (SEC)
| ID | Description |
| SAML 2.0 plugin | |
| 5501 | Artifact Message |
| 5502 | Artifact Resolve Message |
| 5505 | Artifact Response Message |
| 5508 | Authentication Request Message |
| 5510 | Logout Request Message |
| 5511 | Plain Text Assertion |
| 5511 | Logout Response Message |
| 5516 | Response Message |
| 5521 | Passive Response Sent To Service Provider |
| 5522 | Certificate Validation Succeeded |
| 5523 | Certificate Validation Failed |
| 5530 | Signature Validation Succeeded |
| 5531 | Signature Validation Failed |
| 5532 | Resolve Certificate Succeeded |
| 5533 | Resolve Certificate Failed |
| 5540 | Error Empty Response |
| WSFed plugin | |
| 3112 | WSFederation Security Token Validation Error |
| 3117 | Sign In Request Message |
| 3118 | Sign In Response Message |
| 3119 | Sign Out Clean up Request Message |
| 3120 | Sign Out Request Message |
| Username & Password plugin | |
| 4513 | Username Password Authentication Success |
| 4514 | Username Password Authentication Failed |
| NemID plugin | |
| 3315 | NemId Common Log On Error |
| 3316 | NemId Authentication Succeed |
| 3317 | NemId Signature Error |
| 3318 | NemId Validation Error |
| OTP plugin | |
| 4412 | Otp Code Generated |
| 4413 | Otp Code Authentication Success |
| 4414 | Otp Code Authentication Failed |
| Facebook plugin | |
| 3711 | Facebook Response Error |
| 3713 | Facebook Response Message |
| 3714 | Facebook Request Message |
| 3715 | Facebook Access Token Request Message |
| 3718 | Facebook State Code Missing |
| 3717 | Facebook Access Token Response Message |
| Google plugin | |
| 3911 | Google Response Error |
| 3913 | Google Response Message |
| 3914 | Google Request Message |
| 3915 | Google Access Token Request Message |
| 3918 | Google State Code Missing |
| 3917 | Google Access Token Response Message |
| Twitter plugin | |
| 3811 | Twitter Response Error |
| 3813 | Twitter Response Message |
| 3814 | Twitter Request Message |
| 3815 | Twitter Access Token Request Message |
| 3818 | Twitter State Code Missing |
| 3817 | Twitter Access Token Response Message |
| LinkedIn plugin | |
| 4111 | LinkedIn Response Error |
| 4113 | LinkedIn Response Message |
| 4114 | LinkedIn Request Message |
| 4115 | LinkedIn Access Token Request Message |
| 4118 | LinkedIn State Code Missing |
| 4117 | LinkedIn Access Token Response Message |
| Device-Based plugin | |
| 4013 | User Device Cookie Validation Succeeded |
| 4014 | User Device Cookie Validation Failed |
| LiveId plugin | |
| 4311 | LiveId Response Error |
| 4313 | LiveId Response Message |
| 4314 | LiveId Request Message |
| 4315 | LiveId Access Token Request Message |
| 4318 | LiveId State Code Missing |
| 4317 | LiveId Access Token Response Message |
| Ldap plugin | |
| 4713 | Ldap Authentication Succeeded |
| 4714 | Ldap Authentication Failed |
| 4716 | Ldap Reset Password Succeeded |
| 4718 | Ldap Reset Password Failed |
| Yubico plugin | |
| 5205 | Yubico Response Succeeded |
| 5206 | Yubico Response Failed |
| 5203 | Yubico Request Message |
| 5204 | Yubico Response Message |
| Generic Provider plugin | |
| 4814 | Generic Provider Authentication Succeeded |
| 4815 | Generic Provider Authentication Failed |
| STS | |
| 5600 | Client certificate validation is successful on STS |
| 5601 | Client certificate validation is failed,e.g expired client certificate on STS |
| 5602 | The soap request message is signed correctly. |
| 5603 | The soap request message is validated failed..//not logged yet due to a technical issue |
| 5604 | The received RST from User system |
| 5605 | The sent RSTR to User system |
| 5606 | The request with credential is successfully authenticated. |
| 5607 | Invalid credentials. |
| 5608 | Authentication for actas user is passed. |
| 5609 | Authentication for actas user is failed (the reason is also included) |
| 5610 | Authorization for actas user is passed. |
| 5611 | Authorization for actas user is failed (the reason is also included) |
Appendix C: List of Event IDs for Billing log (BIL)
| ID | Description |
| 7000 | Billing log for passive flow |
| 7001 | Billing log for STS flow |
| 7003 | Billing log for provisioning data (REST API) |
Appendix D: List of Event IDs for Revision log (REV)
| ID | Description |
| 20028 | Revision log for create/delete/update resources, user requests which are done via both UI and REST API. |
