We have reworked Identify configurator to not only handle installation and rollback better but also make it easier to support new functionality. The first functionality we have added for Identify configurator 5.0 is the ability to backup databases. You can fairly expect more useful functionality in upcoming versions.
Tenant Creation
Introduction
Creating a new tenant is a complex process comprising of 28 actions.
If any action fails, a rollback process will start which will rollback all executed actions in reversed order. For example, if 3rd action “Import or create signing certificate” fails, rollback process will comprise of:
3. ACTION: “Import or create signing certificate” ->
2. ACTION: “Import or create SSL certificate” ->
1. ACTION: “Create folder structure for Identify”
Detail
ACTION 1: “Create folder structure for Identify”
Description: This action will create folder structure of creating tenant. By default, root folder is created in ‘C:\Program Files\Safewhere\Identify\Tenants’, and named by tenant Id.
It includes sub-folder: admin, runtime, service, Logs.
Rollback: Rollback of this action will delete the root folder (C:\Program Files\Safewhere\Identify\Tenants\[TenantId])
ACTION 2: “Import or create SSL certificate”
Description: This action will import SSL certificate to Store.
It depends on the SSL certificate selection which is set on UI:
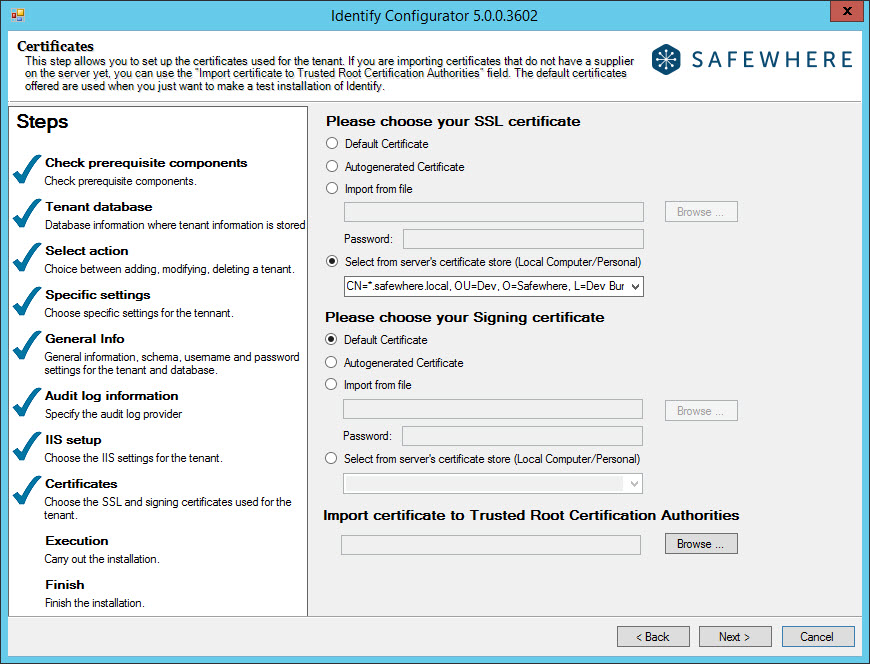
* If user chooses “Default Certificate”, this step will import default SSL certificate to Store.
* If user chooses “Auto generated Certificate”, this step will create a SSL certificate and import to Store.
* If user chooses “Import from file”, and selects a file, this step will import selected file to store. If SSL certificate has been already in store before, it will be ignored.
* If user chooses “Selected from server’s certificate store”, the list of the valid certificates from LocalMachine/Personal will be loaded.
Rollback: Rollback of this action will delete SSL certificate from store if it has not already existed before the action ran.
ACTION 3: “Import or create signing certificate”
Description: This action will import signing certificate to Store. It depends on the signing certificate selection that set on UI

* If user chooses “Default Certificate”, this step will import default signing certificate to Store.
* If user choose “Auto generated Certificate”, this step will create a signing certificate and import to Store.
* If user chooses “Import from file”, and selects a file, this step will import selected file to store.If the selected SSL certificate has been already in store, this step will be ignored.
* If user chooses “Selected from server’s certificate store”, the list of the valid certificates from LocalMachine/Personal will be loaded.
Rollback: Rollback of this action will delete signing certificate from store if it has not already existed before the action ran.
ACTION 4: “Import Trusted Root Authority certificate”
Description: This action will import the chosen CA certificate to Store

If user chooses nothing, this step will be ignored.
Rollback: Rollback of this action will remove this certificate from store if it has not already existed before the action ran.
ACTION 5: “Grant access to SSL certificate”
Description: This action will grant access permission to the SSL certificate private key.
The granted user will depend on the chosen authentication at the step General info of UI
* If user chooses to login by WindowAuthentication, the granted user will be the added domain user.
* If user chooses to login by SQLDatabaseAuthentication, the granted user will be the Network service.
Rollback: Rollback of this action will remove granted permission.
ACTION 6 : “Grant access to signing certificate”
Description: This action will grant access permission to the signing certificate private key.
The granted user will depend on the chosen authentication at the step General info of UI

* If user chooses to login by WindowAuthentication, the granted user will be the added domain user.
* If user chooses to login by SQLDatabaseAuthentication, the granted user will be the Network service.
Rollback: Rollback of this action will remove granted permission.
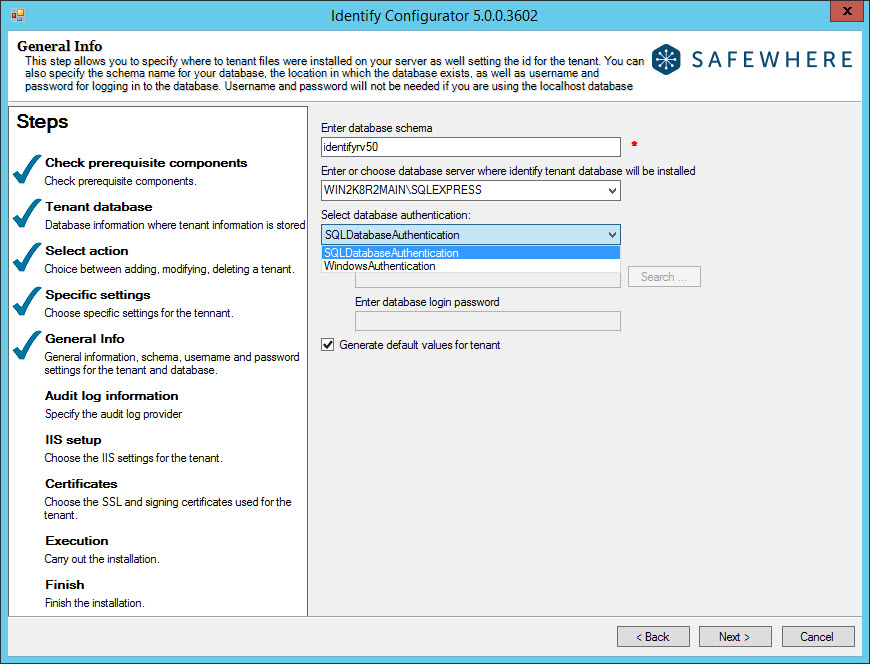
ACTION 7: “Setup Identify Database”
Description: This action will create the Identify database for this tenant.
Rollback: Rollback of this action will remove the Identify database for this tenant.
ACTION 8: “Install Session Database”
Description: This action will create the Session database for this tenant.
Rollback: Rollback of this action will remove the Session database for this tenant.
ACTION 9: “Install Cache Database”
Description: This action will create the Cache database for this tenant.
Rollback: Rollback of this action will remove the Cache database for this tenant.
ACTION 10: “Install Audit Database”
Description: This action will create the Audit database for this tenant.
Rollback: Rollback of this action will remove the Audit database.
ACTION 11: “Install Claims Filter Database”
Description: This action will create the [FilterExcludedClaims] table, the [FilterClaimsChanged] table into the Identify database for this tenant.
Rollback: Rollback of this action will be skipped because these tables will be deleted on the prior “Setup Identify Database” step.
ACTION 12: “Install Unp Database”
Description: This action will create the view [NameClaimTypedUserCredential], create the user/password login into Identify database for this tenant
Rollback: Rollback of this action will be skipped because they will be deleted on the prior “Setup Identify Database” step.
ACTION 13: “Install Admin Web Application”
Description: This action will create the event source ‘Identify[TenantId] – Admin’ and ‘Identify [TenantId]’ in the event log “Safewhere” at the event viewer.
Rollback: Rollback of this action will remove the event source ‘Identify[TenantId] – Admin’ and ‘Identify [TenantId]’. If these is only one tenant, the event log source “Safewhere” will also be deleted.
ACTION 14 : “Install runtime”
Description: This action will create the event source ‘Identify[TenantId] – Runtime’ in the event log “Safewhere” at the event viewer
Rollback: Rollback of this action will remove the event source ‘Identify[TenantId] – Runtime’.
ACTION 15: “Install WCF Service”
Description: This action will create the event source ‘Identify[TenantId] – Service’ and ‘Identify[TenantId] – Management’ in the event log “Safewhere” at the event viewer
Rollback: Rollback of this action will remove the event source ‘Identify[TenantId] – Service’ and ‘Identify[TenantId] – Management’.
ACTION 16: “Setup Website”
Description: This action will create application pool and website for Admin, Runtime and service.
Rollback: Rollback of this action will delete them.
ACTION 17: “Modifying Web.config”
Description: This action will replace string on web.config of admin, runtime, service.
* For admin website, it includes: #SCHEMA, #SERVER, #LOGIN_CREDENTIAL, #TENANT_DOMAIN, #CERT_SIGNING_THUMBPRINT,
#LOG_FOLDER_PATH, #AUDIT_LOG_PROVIDER, #CONNECTION_STRING_AUDIT_LOG_PROVIDER, #SESSION_STATE_MODE, #SQL_STATE_SERVER_CONNECTION_STRING, #TIMEOUT,
* For runtime website, it includes: #SCHEMA, #RUNTIME_TENANT_PATH, #LOG_FOLDER_PATH, #CLIENT_NAME, #DEFAULT_LANGUAGE, #AUDIT_LOG_PROVIDER, #LOGIN_CREDENTIAL,
#CONNECTION_STRING_AUDIT_LOG_PROVIDER, #TIMEOUT, #SESSION_STATE_MODE, #SQL_STATE_SERVER_CONNECTION_STRING
* For Service, it includes: #TENANT_DOMAIN, #CERT_SIGNING_THUMBPRINT, #CONNECTION_STRING_AUDIT_LOG_PROVIDER, #SERVER, #LOGIN_CREDENTIAL, #SCHEMA,
#AUDIT_LOG_PROVIDER, #LOG_FOLDER_PATH, #CERT_SIGNING_THUMBPRINT
Rollback: Rollback of this action will be skipped because web.config files will be deleted on the prior steps.
ACTION 18: “Encrypt Connection String”
Description: This action will encrypt connection string in web.config.
Rollback: Rollback of this action will be skipped because web.config file will be deleted at the prior steps.
ACTION 19: “Encrypt Session State Connection String”
Description: This action will encrypt Session State Connection String in web.config.
Rollback: Rollback of this action will be skipped because web.config file will be deleted on the prior steps.
ACTION 20: “Append Hosts File”
Description: This action will add the tenant domain to \system32\drivers\etc\hosts file.
Rollback: Rollback of this action will remove the added domain from host file.
ACTION 21: “Save Tenant Configuration”
Description: This action will insert the new tenant record into the table Tenant of the IdentifyTenant database.
Rollback: Rollback of this step will remove this record from the table Tenant of the IdentifyTenant database.
ACTION 22: “Set delegation of ‘Authentication – Anonymous’, ‘Authentication – Forms’ and ‘Authentication – Windows’ to Read/Write”
Description: This step will set feature delegation of ‘Authentication – Anonymous’ and ‘Authentication – Windows’ to Read/Write on IIS
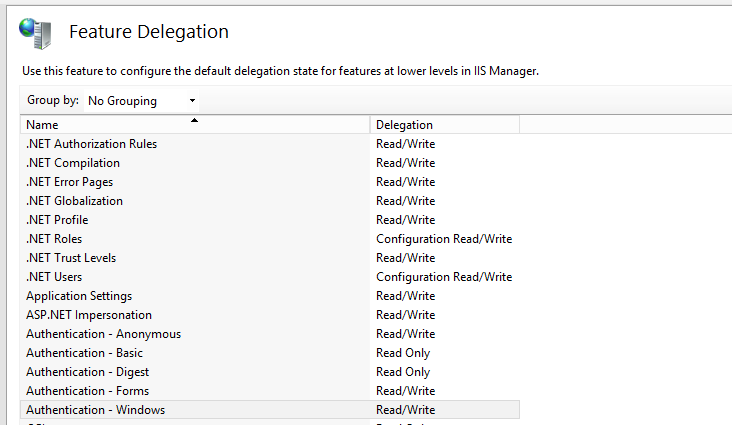
Rollback: Rollback of this action will set these features to their former state.
ACTION 23: “Add Security.Cryptography.dll into GAC”
Description: This action will add Security.Cryptography.dll to GAC library.
Rollback: Rollback of this action will remove this file if it has been added to GAC library by the action itself. Otherwise, if this file has already been added before, the configurator will not remove it.
ACTION 24: “Set User Rights Assignment for ‘Generate Security Audits’ privilege”
Description: This action will add User for Generate Security Audits
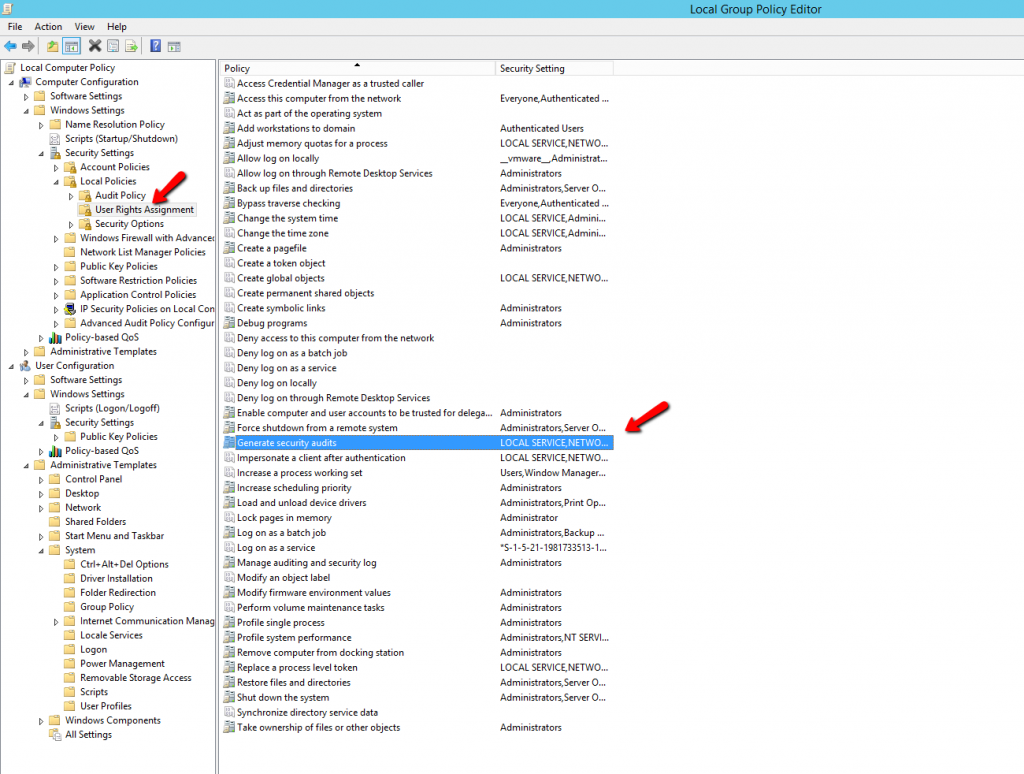
Rollback: Rollback of this action will remove the user if it not added before.
ACTION 25: “Register RSASHA256 Algorithm into machine config for both .net 2.0 and 4.0 in both 32 and 64 bits.”
Description: This action will register RSASHA256 Algorithm into machine.config files for: .NET 2.0 32 bits(C:\Windows\Microsoft.NET\Framework\v2.0.50727\CONFIG), .NET 2.0 64 bits (C:\Windows\Microsoft.NET\Framework64\v2.0.50727\CONFIG), .NET 4.0 32bits(C:\Windows\Microsoft.NET\Framework\v4.0.30319\CONFIG), .NET 4.0 64 bits(C:\Windows\Microsoft.NET\Framework64\v4.0.30319\CONFIG). If the RSASHA256 Algorithm has registered before, this step will be skipped.
Rollback: Rollback of this action will unregister RSASHA256 Algorithm for both .net 2.0 and 4.0 in both 32 and 64 bits. If RSASHA256 Algorithm has been registered before, this step will be skipped.
ACTION 26: “Register Windows Security Log for Identify”
Description: This action will register Windows Security log for creating tenant. It will copy file IdentifySecurityLoggingMessage.dll to C:\Temp\[TenantId] then run GAD.Installer.exe
to register. The folder c:\Temp\[TenantId] will be deleted after completion.
Rollback: Rollback of this action will unregister Windows Security log for the creating tenant.
27. ACTION: “Update Configurator Information”
Description: This action will update Configurator information at the file C:\Program Files\Safewhere\Identify\Tools\Configurator.txt by adding the tenantID to ‘TenantIds’ section.
Rollback: Rollback of this action will remove tenantId from the Configurator.txt file.
ACTION 28: “Unlock Web Config Action”
Description: This action will unlock section system.webServer/serverRuntime on applicationhost file.
Rollback: Rollback of this action will remove the update at this step.
Tenant Upgrade
Introduction
Upgrading a tenant is a complex process comprising of 20 actions with rollback support.
Detail
ACTION 1: “Stop the upgrading website”
Description: This action will stop the upgrading website
Rollback: Rollback of this action will start the upgrading website.
ACTION 2: “Load Tenant Configuration and put them into the Container”
Description: This action will load the configuration of upgrading tenant from the table Tenant at the IdentifyTenant database. This configuration includes the tenant setting, the website setting and the database setting which will be used for the next action.
Rollback: Rollback of this action will be skipped because it only reads information.
ACTION 3: “Explore Admin Webconfig from .NET 4.5 framework: Find the current signing certificate and use it if possible. “
Description: This action will get the signing certificate from web.config at the Admin following the path: configuration/system.identityModel.services/federationConfiguration/serviceCertificate/certificateReference. This certificate will be used in action “Update Tenant Configuration”.
Rollback: Rollback of this action will be skipped because it only reads information.
ACTION 4: “Explore Admin Webconfig For Tenant Before Upgrading 4.5 framework: Find the current signing certificate and use it if possible. “
Description: In case the upgraded tenant is using .NET 4.0 framework, this action will get the signing certificate from web.config at the Admin following the path: configuration/microsoft.identityModel/service/serviceCertificate/certificateReference. This certificate will be used in action “Update Tenant Configuration”.
Rollback: Rollback of this action will be skipped because it only reads information.
ACTION 5: “Zip and backup folder”
Description: This action will backup folder ‘C:\Program Files\Safewhere\Identify\Tenants\[TenantId]’ into a zip file. It does not include log folder.
Rollback: This action doesn’t need rollback.
ACTION 6: “Upgrade folder for tenant”
Description: This action will:
– Delete all files and sub-directories of the admin directory except the *.license files.
– Delete all files and sub-directories of the runtime directory except the *.license files and the DiagnosticsLog directory.
– Delete all files and sub-directories of the service directory except the *.license files.
Rollback: Rollback of this action will unzip the zip file that is created at ACTION 5: “Zip and backup folder”. Then configurator will grant full permission to the folders for the application pool user..
ACTION 7: “Grant full permission”
Description: This action will grant full permission for all folder: admin, runtime, service, Logs, runtime\DiagnosticsLog,
Rollback: Rollback of this action will be skipped.
ACTION 8: “Modifying Web.config”
Description: This action will replace string on web.config of admin, runtime, service.
* For admin website, it includes: #SCHEMA, #SERVER, #LOGIN_CREDENTIAL, #TENANT_DOMAIN, #CERT_SIGNING_THUMBPRINT,
#LOG_FOLDER_PATH, #AUDIT_LOG_PROVIDER, #CONNECTION_STRING_AUDIT_LOG_PROVIDER, #SESSION_STATE_MODE, #SQL_STATE_SERVER_CONNECTION_STRING, #TIMEOUT,
* For runtime website, it includes: #SCHEMA, #RUNTIME_TENANT_PATH, #LOG_FOLDER_PATH, #CLIENT_NAME, #DEFAULT_LANGUAGE, #AUDIT_LOG_PROVIDER, #LOGIN_CREDENTIAL,
#CONNECTION_STRING_AUDIT_LOG_PROVIDER, #TIMEOUT, #SESSION_STATE_MODE, #SQL_STATE_SERVER_CONNECTION_STRING
* For Service, it includes: #TENANT_DOMAIN, #CERT_SIGNING_THUMBPRINT, #CONNECTION_STRING_AUDIT_LOG_PROVIDER, #SERVER, #LOGIN_CREDENTIAL, #SCHEMA,
#AUDIT_LOG_PROVIDER, #LOG_FOLDER_PATH, #CERT_SIGNING_THUMBPRINT
Rollback: Rollback of this action will be skipped because the web.config files are overwritten after the rollback at ACTION 6: “Upgrade folder for tenant”
ACTION 9: “Encrypt Connection String”
Description: This action will encrypt connection string in web.config.
Rollback: Rollback of this action will be skipped because the web.config files are overwritten after the rollback at ACTION 6: “Upgrade folder for tenant”
ACTION 10: “Encrypt Session State Connection String”
Description: This action will encrypt Session State Connection String in web.config.
Rollback: Rollback of this action will be skipped because the web.config files are overwritten after the rollback at ACTION 6: “Upgrade folder for tenant”
ACTION 11: “Set delegation of ‘Authentication – Anonymous’, ‘Authentication – Forms’ and ‘Authentication – Windows’ to Read/Write”
Description: This step will set feature delegation of ‘Authentication – Anonymous’ and ‘Authentication – Windows’ to Read/Write on IIS

Rollback: Rollback of this action will set these features to their former states.
ACTION 12: “Set User Rights Assignment for ‘Generate Security Audits’ privilege”
Description: This action will add User for Generate Security Audits

Rollback: Rollback of this action will remove the user if it is added by this action itself.
ACTION 13: “Register Windows Security Log for Identify”
Description: This action will register Windows Security log for creating tenant. It will copy file IdentifySecurityLoggingMessage.dll to C:\Temp\[TenantId] then run call GAD.Installer.exe
to register. Then the folder c:\Temp\[TenantId] will be deleted after it’s completed.
Rollback: Rollback of this action will unregister Windows Security log for the tenant.
ACTION 14: “Unlock Web Config Action”
Description: This action will unlock section system.webServer/serverRuntime on applicationhost file.

Rollback: Rollback of this action will remove the update that is done by this step.
ACTION 15: “Update Tenant Configuration”
Description: This action will update Configurator information including the latest upgrade datetime and version of upgrading Tenant on the IdentifyTenant database.
Rollback: Rollback of this action will reverse to the former upgrade datetime and version.
ACTION 16: “Install Admin Web Application”
Description: This action will create the event source ‘Identify[TenantId] – Admin’ and ‘Identify [TenantId]’ in the Windows event log “Safewhere”.
Rollback: Rollback of this action will remove the event source ‘Identify[TenantId] – Admin’ and ‘Identify [TenantId]’. If this is the only one tenant, the event log “Safewhere” will be deleted.
ACTION 17: “Install runtime”
Description: This action will create the event source ‘Identify[TenantId] – Runtime’ in the Windows event log “Safewhere”
Rollback: Rollback of this action will remove the event source ‘Identify[TenantId] – Runtime’.
ACTION 18: “Install WCF Service”
Description: This action will create the event source ‘Identify[TenantId] – Service’ and ‘Identify[TenantId] – Management’ in the Windows event log “Safewhere”
Rollback: Rollback of this action will remove the event source ‘Identify[TenantId] – Service’ and ‘Identify[TenantId] – Management’.
ACTION 19: “Extract Change Script”
Description: this action will do a few steps:
- Backup the Identify database if the option “Backup database” is checked.
- Execute upgrade change script as follow:
- For SQL server: All scripts will run on a transaction.
- For Azure SQL as a service: All scripts will be split and run in many smaller transactions per database: Identify, IdentifyAudit, IdentifyCache, IdentifySession, IdentifySessionState.
Rollback:
- For SQL server: if all scripts finish successfully, configurator will commit the transaction. If any error occurs, the transaction will be rollbacked at the rollback step.
- For Azure SQL as a service: if all scripts finish successfully, configurator will commit these transactions. If any transaction fails to commit, all uncommitted transactions will be rollbacked and configurator will write a log entry that says “Cannot rollback changes for databases: {0} because transactions have been committed. Please rollback them manually.”
ACTION 20: “Start the upgraded website”
Description: This action will start the Identify web site after upgrade completes.
Rollback: this step doesn’t make any change and thus doesn’t support rollback. If this action fails, configurator will write a log entry “Cannot start Web site. Please check using port and start it manually.” then stop immediately.
