Requirement
From the user detail page, it must be possible to select which services the user can do act-as for.
How the ActAs function works at UserLevel
There is a requester (named as A, let’s say A is a local user and have a list of actas-authorized-service-uris) who executes issue request having
- ActAs element as a saml2 token or a x509 certificate (named as B)
- AppliesTo: is a service is secured by this issued token
When process this request, Identify will response a security token having claims extracted from A and B (depends on our settings)
To do the ActAs authorization successfully, the ActAs user must have:
- He’s a Identify local user
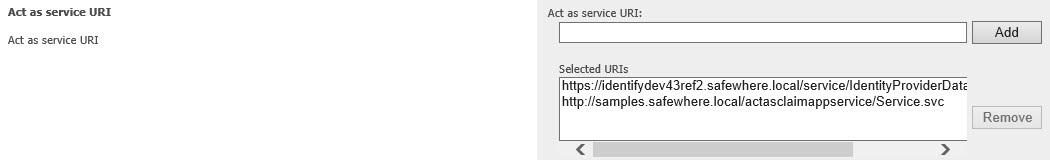
- The AppliesTo must be one of his service URI list at his user form:
Besides, the comparison between the AppliesTo and one of his service URI list is Equal.
How the ActAs function work at connection
On the WSFED protocol connection, we have the new control:
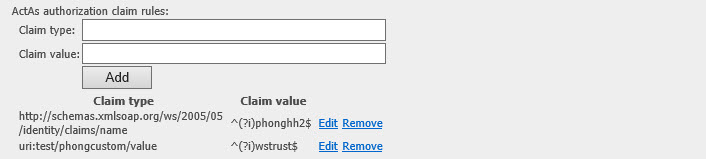
ActAs User needs to have at least 1 claim type matching with the ones on this setting to do the ActAs authorization successfully.
Note: This setting hasn’t worked for local user yet, but ADFS user. We will finish supporting it in one of the next weekly updates for version 4.3.
